Elements of a Successful Cloud Security Program

This week I gave a presentation at the RSA Conference titled “Walking on Broken Clouds” (Slides).

© 2014 Paul Kelley - oil on panel; 8 x 10 inches
Cloud Security in 2023 is the same dumpster fire it was back in 2017. Organizations have a hundred thousand CSPM findings. There aren’t enough security architects and the providers are releasing new services all the time. This session will talk through some successes and failures had in building a cloud security program and cover what worked, what was a waste of time, and a few new things to try.
I was asked to present on “What worked, what didn’t, and what was a waste of time”. This post defines more of what elements make up a successful program with less focus on what didn’t work.
Objectives of a Cloud Security Program:
- Reduce the risk to the business (as it relates to all things public cloud)
That’s it. That’s the objective. Reduce the business’s risk.
Outcomes of a successful Cloud Security Program:
- Don’t get breached
- Don’t have audit findings
- Don’t move so slowly your company becomes irrelevant
- Don’t spend so much you go out of business
This is not an ordered list. You have to decide for your organization which is the biggest threat: the Russians or the Auditors? Is your business model growing, or are you in the midst of disruption? Yes, you can turn on every security service and tell the CISO you did so, but is that fiscally sustainable?
So we’ve set out the high-level objectives and outcomes, how do you actually do it.
Building a successful Cloud Security Program
To build a successful program, you want to:
- Know your company’s threat model.
- How is the money made?
- Where are the things that others want (content, PII, crypto-wallet keys, etc)?
- What are the necessary exposed surfaces?
- What is management’s appetite for risk?
- What is their appetite for risk based on what they say?
- What is their appetite for risk based on how they act?
- Codify your cloud security best practices.
- This could be a standard or baseline document, but be wary of the GRC Trap.
- Focus on what is meaningful and achievable in your organization.
- Make the document approachable to the builders (developers, sysadmins, SREs, etc).
- Define your mission.
The Cloud Security Program supports the security team’s broader mission of incident response, vulnerability management, and compliance, while acting as subject matter experts for development and operations.
- Establish Cloud Security Key Risk Indicators (KRIs).
- Make friends with your builders.
- Focus on outcomes not tools.
- Builders don’t care that you bought a new CNAPP solution. They really don’t care that you want them to deploy new agents in all their workloads.
- Articulate the risks your efforts are tying to mitigate.
- Remain focused on outcomes
- Don’t let them weaponize your cloud security program for compliance or pre-merger posturing.
On Shifting Left
Build your program with the builders, not policy & compliance in mind.
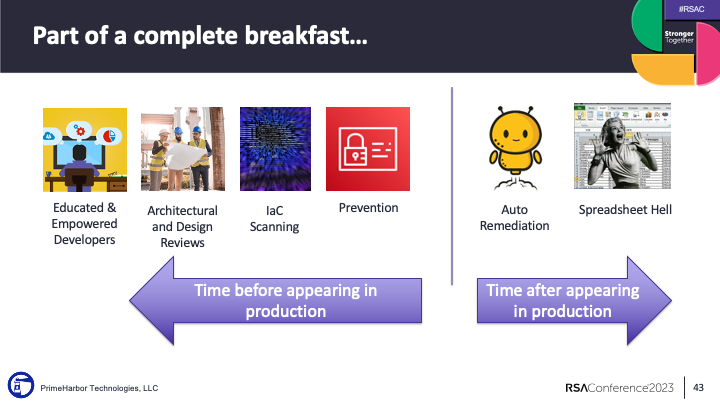
The wrong way to build a cloud security program is to start on the right. Finding all the problems, putting them in a spreadsheet, and sending them to your account owners.
The right mindset is to start with your builders.
- Educate them on the risk of public cloud.
- Work with them on threat modeling and secure architectural reviews
- Help them implement security scanning into the Infrastructure-as-code deployment process
Then you can start to implement governance controls like Service Control Policies to prevent misconfigurations, or tools like Turbot or CloudCustodian to autoremediate the issues.
Whatever remains, that small pile of residual risk, can go on a spreadsheet or get opened as a ticket with the team that needs to remediate the issue.